Dataset Description The advancements in the field of telecommunications have resulted in an increasing demand for robust, high-speed, and secure connections between User Equipment (UE) instances and the Data Network (DN). The implementation of the newly defined 3rd Generation Partnership Project 3GPP (3GPP) network architecture in the 5G Core (5GC) represents a significant leap [...]
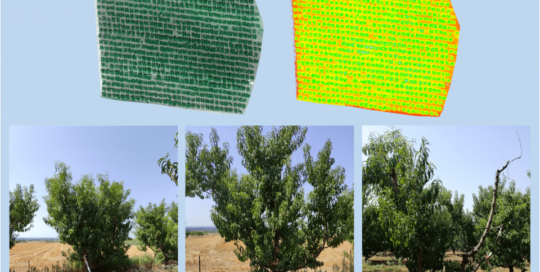
Peach Tree Disease Detection Dataset
panagiotisrg2023-01-14T16:35:24+03:00Peach Tree Disease Detection Dataset This peach tree disease detection dataset is a multimodal, multi-angle dataset which was constructed for monitoring the growth of peach trees, including stress analysis and prediction. An orchard of peach trees is considered in the area of Thessaly, where 889 peach trees were recorded in a full crop season starting [...]
DNP3 Intrusion Detection Dataset
panagiotisrg2022-12-17T15:21:18+03:00Dataset Description In the digital era of the Industrial Internet of Things (IIoT), the conventional Critical Infrastructures (CIs) are transformed into smart environments with multiple benefits, such as pervasive control, self-monitoring and self-healing. However, this evolution is characterised by several cyberthreats due to the necessary presence of insecure technologies. DNP3 is an industrial communication protocol [...]
Cherry Tree Disease Detection Dataset
panagiotisrg2023-01-14T16:30:31+03:00Dataset Description This cherry tree disease detection dataset is a multimodal, multi-angle dataset which was constructed for monitoring the growth of cherry trees, including stress analysis and prediction. An orchard of cherry trees is considered in the area of Western Macedonia, where 577 cherry trees were recorded in a full crop season starting from [...]
IEC 60870-5-104 Intrusion Detection Dataset
panagiotisrg2022-12-12T00:43:29+03:00Dataset Description The evolution of the Industrial Internet of Things (IIoT) introduces several benefits, such as real-time monitoring, pervasive control and self-healing. However, despite the valuable services, security and privacy issues still remain given the presence of legacy and insecure communication protocols like IEC 60870-5-104. IEC 60870-5-104 is an industrial protocol widely applied in [...]